Automatically discover hidden relationships and patterns using: automatic filtering, linking, network analysis, geo-location; AI, face and object recognition; Bot detection, time-series analysis, clustering and segmentation, NLP technology, Named Entity Recognition (NER), language detection and translators, OCR, sentiment analysis and text transcription from audio and video.
Threat Monitoring and Alerting
Supporting the entire Intelligence Lifecycle, Hunter fuses internal and external data with powerful analytics for comprehensive threat detection and tracking.
REQUEST A DEMOHunter’s OSINT Fusion Center is a versatile platform that spans the entire intelligence cycle. It seamlessly integrates data from multiple sources and languages, presenting both static findings and an interactive “hunting” interface. Analysts can manually post-process collected data, enabling the development of operational insights and refinements. Tracker can be deployed on-premise or in the cloud, offering flexibility to suit organizational needs.
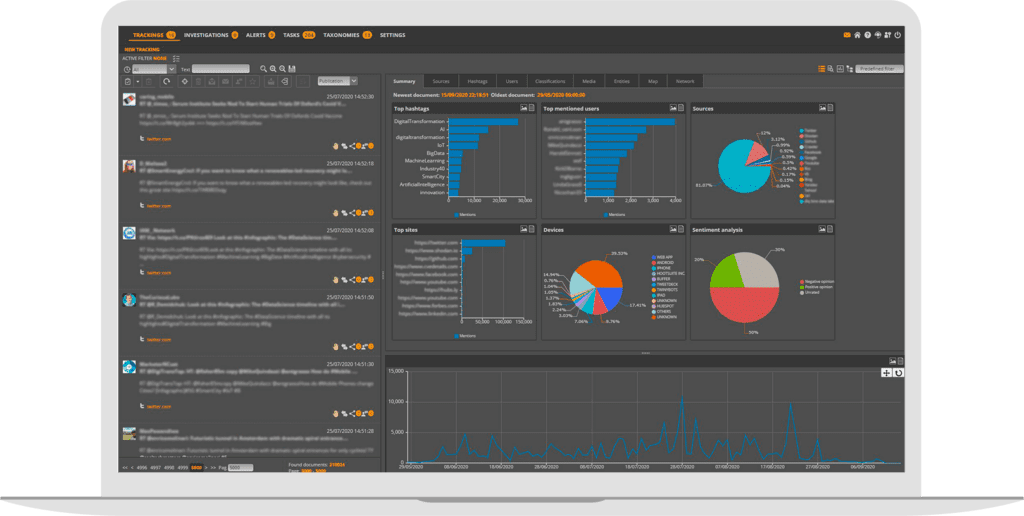
Full spectrum data coverage
Collect and fuse internal and external data from surface to dark web, including hundreds of connectors from Social Media, forums and our proprietary breach data lake: the largest of its kind with over 180 billion attributes and 124 billion curated identity records spanning 125 countries and 53 languages.
Real-time dashboards, reports, and alerts
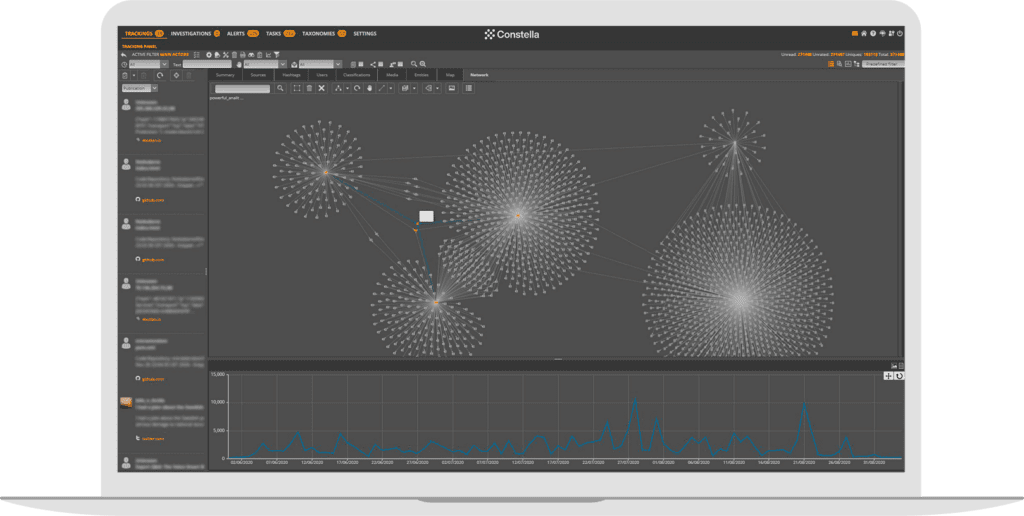
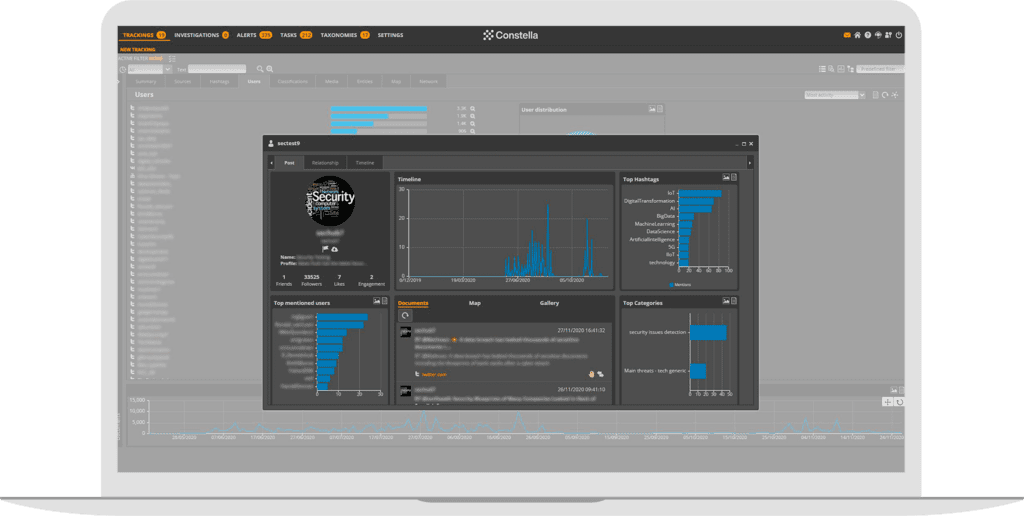
Asset protection and tracking workspace
Increase efficiency of digital surveillance, threat monitoring, situational awareness and early warning—monitoring specific assets (companies, personas, domains, etc.) through advanced filtering configuration, pattern matching and automatic entity extraction
Multiple case management workspace
Perform highly efficient, collaborative investigations with managed workflows: generate new case files, create personas/entities relationship graphs, selectively share insights, filter and extract content, create associations, save and manage multiple cases
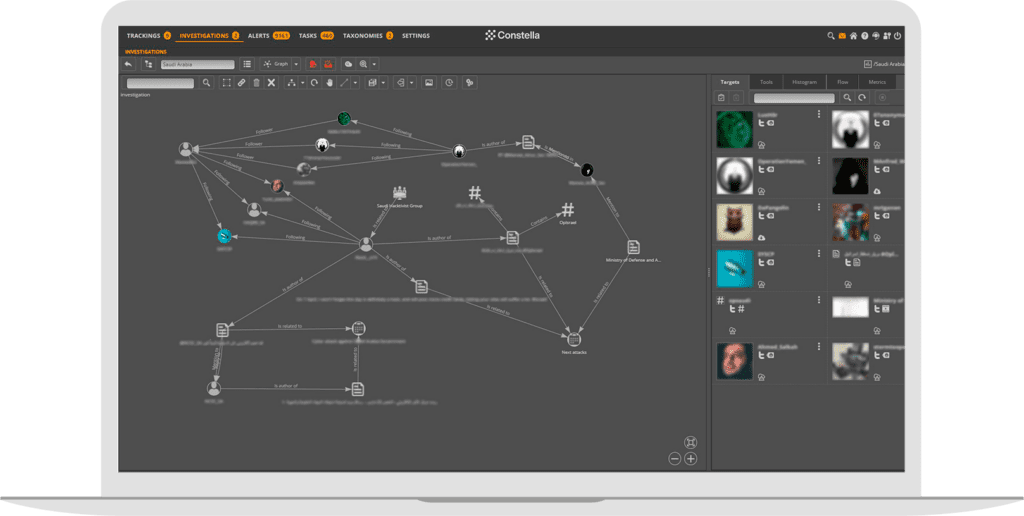
Multi-tenant, secure, scalable collaboration
Support different organizations (for MSSPs), missions or Intel Units (for Enterprises or LEAs) with granular access controls, permissions and sharing policies to isolate sensitive information and workspaces—configuring, scheduling and managing thousands of collection tasks/policies.
Powerful analytics and automation
Custom threat intelligence models
Define and implement specific threat models for companies or verticals/use cases by defining taxonomies, assets, sources, trackings, and filters—reducing customers’ risk profile through a more relevant, accurate, and efficient threat intelligence workflow.
Fully supported intelligence cycle
Support the entire intelligence workflow of an analyst for increased efficiency and real-time, actionable intelligence—from planning & direction through to collection, processing & storage, analysis, and dissemination of intelligence.
Constella.ai is the global leader in AI-driven identity risk and deep and dark web intelligence for such applications as identity theft, insider risk, synthetic identity fraud detection (Advanced KYE/KYB), and deep OSINT investigations.
With the world’s largest breach database, containing over one trillion data attributes in 125+ countries and over 53 languages, Constella empowers leading organizations across the globe to monitor and secure critical data through unparalleled visibility and actionable insights.
Digital Risk Protection Platforms
Executive and Brand Digital Protection
Subscribe To The Constella Newsletter
©2025 Constella Intelligence. All rights reserved. Website Privacy Policy. Terms of Use. Acceptable Use Policy.



